文档简介:
限制条件
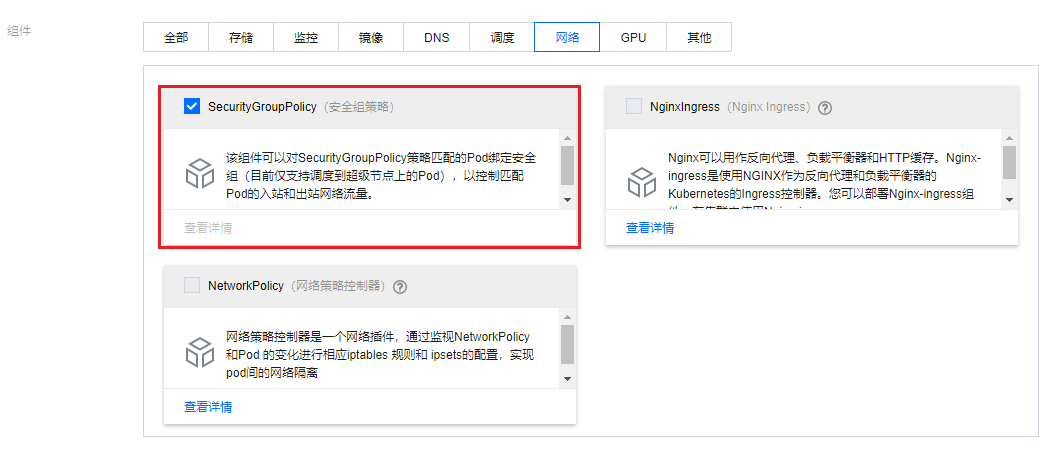
为 Pod 启用安全组能力
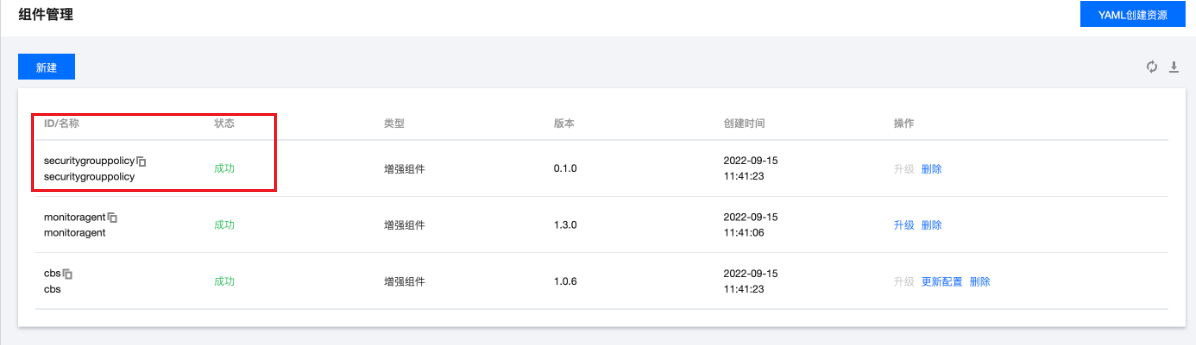
安装扩展组件
部署示例应用程序
使用安全组部署示例 Pod
my_cluster_name=my-clustermy_cluster_vpc_id=$(tccli tke DescribeClusters --cli-unfold-argument
--ClusterIds $my_cluster_name --filter Clusters[0].ClusterNetworkSettings.VpcId | sed 's/\"//g')
my_cluster_security_group_id=$(tccli vpc DescribeSecurityGroups --cli-unfold-argument
--Filters.0.Name security-group-name --Filters.0.Values tke-worker-security-for
-$my_cluster_name --filter SecurityGroupSet[0].SecurityGroupId | sed 's/\"//g')
my_pod_security_group_name=my-pod-security-grouptccli vpc CreateSecurityGroup --GroupName "my-pod-security-group"
--GroupDescription "My pod security group"
my_pod_security_group_id=$(tccli vpc DescribeSecurityGroups
--cli-unfold-argument --Filters.0.Name security-group-name --Filters.0.Values
my-pod-security-group --filter SecurityGroupSet[0].SecurityGroupId | sed 's/\"//g')
echo $my_pod_security_group_id
tccli vpc CreateSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_cluster_security_group_id --SecurityGroupPolicySet.Ingress.0.Protocol
UDP --SecurityGroupPolicySet.Ingress.0.Port 53 --SecurityGroupPolicySet.Ingress.0.S
ecurityGroupId $my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Action ACCEPT
tccli vpc CreateSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_cluster_security_group_id --SecurityGroupPolicySet.Ingress.0.Protocol
TCP --SecurityGroupPolicySet.Ingress.0.Port 53 --SecurityGroupPolicySet.Ingress.
0.SecurityGroupId $my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Action ACCEPT
tccli vpc CreateSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Protocol ALL
--SecurityGroupPolicySet.Ingress.0.Port ALL --SecurityGroupPolicySet.Ingress.
0.SecurityGroupId $my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Action ACCEPT
tccli vpc CreateSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_pod_security_group_id --SecurityGroupPolicySet.Egress.0.Protocol ALL
--SecurityGroupPolicySet.Egress.0.Port ALL --SecurityGroupPolicySet.Egress.0.Action ACCEPT
kubectl create namespace my-namespace
apiVersion: vpcresources.tke.cloud.tencent.com/v1beta1kind: SecurityGroupPolicymetadata:name: my-security-group-policynamespace: my-namespacespec:podSelector:matchLabels:app: my-appsecurityGroups:groupIds:- $my_pod_security_group_id
kubectl apply -f my-security-group-policy.yaml
apiVersion: apps/v1kind: Deploymentmetadata:name: my-deploymentnamespace: my-namespacelabels:app: my-appspec:replicas: 2selector:matchLabels:app: my-apptemplate:metadata:labels:app: my-appspec:terminationGracePeriodSeconds: 120containers:- name: nginximage: nginx:latestports:- containerPort: 80nodeSelector:node.kubernetes.io/instance-type: eklettolerations:- effect: NoSchedulekey: eks.tke.cloud.tencent.com/ekletoperator: Exists---apiVersion: v1kind: Servicemetadata:name: my-appnamespace: my-namespacelabels:app: my-appspec:selector:app: my-appports:- protocol: TCPport: 80targetPort: 80
kubectl apply -f sample-application.yaml
kubectl get pods -n my-namespace -o wide
NAME READY STATUS RESTARTS AGE IP NODE
NOMINATED NODE READINESS GATES
my-deployment-866ffd8886-9zfrp 1/1 Running 0 85s 10.0.64.10 eklet-subnet-q21rasu6-8bpgyx9r <none> <none>my-deployment-866ffd8886-b7gzb 1/1 Running 0 85s 10.0.64.3 eklet-subnet-q21rasu6-8bpgyx9r <none> <none>
kubectl exec -it -n my-namespace my-deployment-866ffd8886-9zfrp -- /bin/bash
curl my-app
<!DOCTYPE html><html><head><title>Welcome to nginx!</title>...
tccli vpc DeleteSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_cluster_security_group_id --SecurityGroupPolicySet.Ingress.0.Protocol UDP
--SecurityGroupPolicySet.Ingress.0.Port 53 --SecurityGroupPolicySet.Ingress.
0.SecurityGroupId $my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Action ACCEPT
tccli vpc DeleteSecurityGroupPolicies --cli-unfold-argument --SecurityGroupId
$my_cluster_security_group_id --SecurityGroupPolicySet.Ingress.0.Protocol TCP
--SecurityGroupPolicySet.Ingress.0.Port 53 --SecurityGroupPolicySet.Ingress.
0.SecurityGroupId $my_pod_security_group_id --SecurityGroupPolicySet.Ingress.0.Action ACCEPT
curl my-app
kubectl delete namespace my-namespacetccli vpc DeleteSecurityGroup --cli-unfold-argument --SecurityGroupId $my_pod_security_group_id






