文档简介:
限制条件
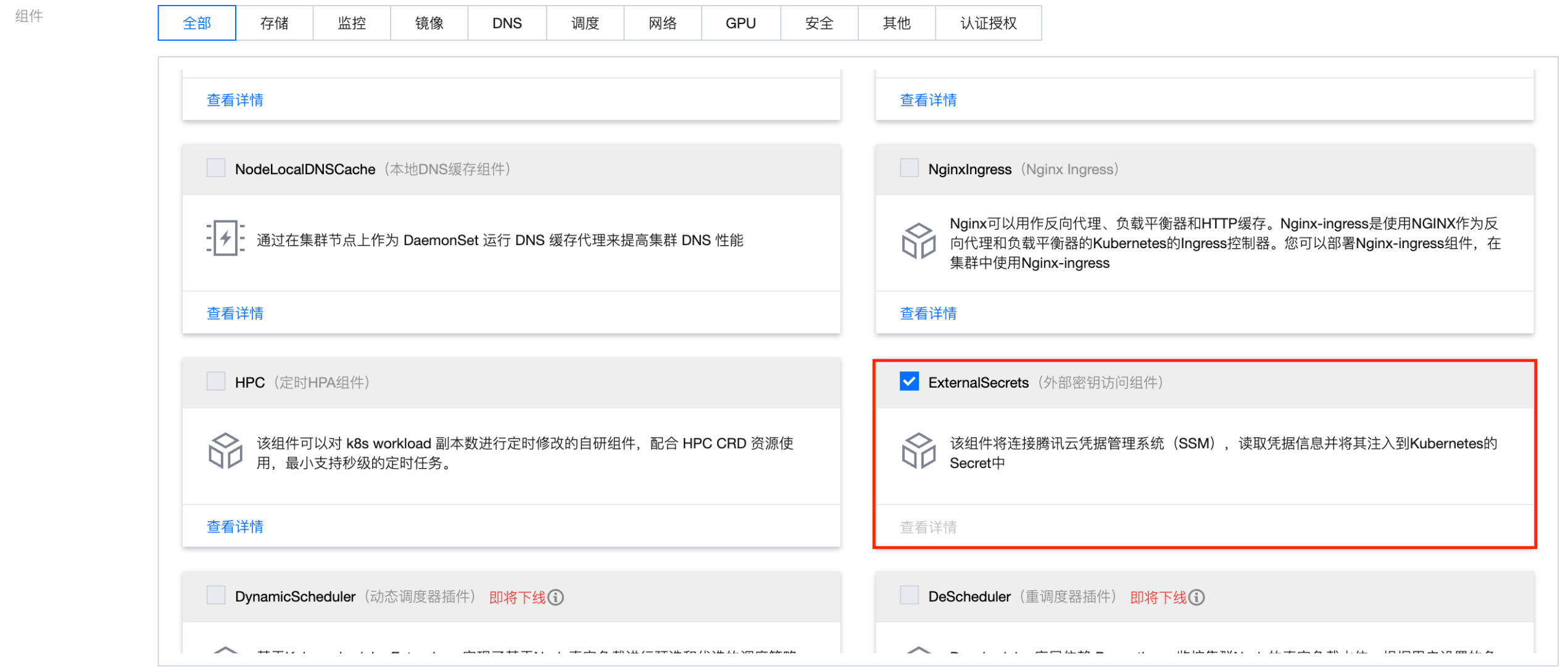
启用外部密钥访问能力
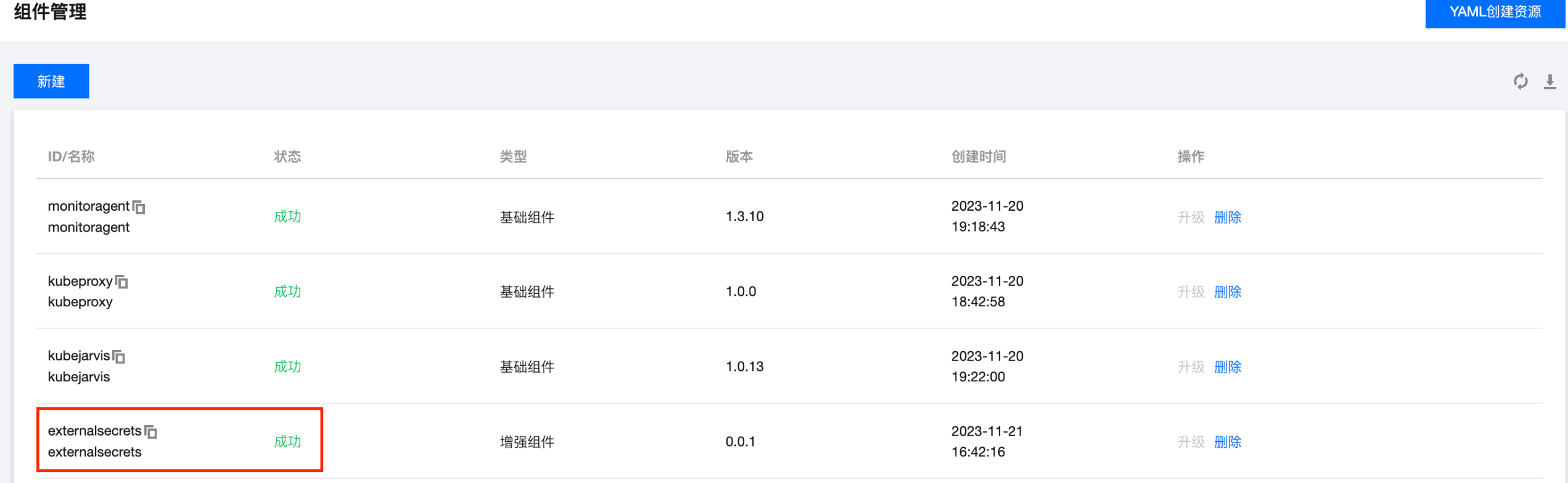
安装扩展组件
使用方式
方式一:通过 AKSK 授权
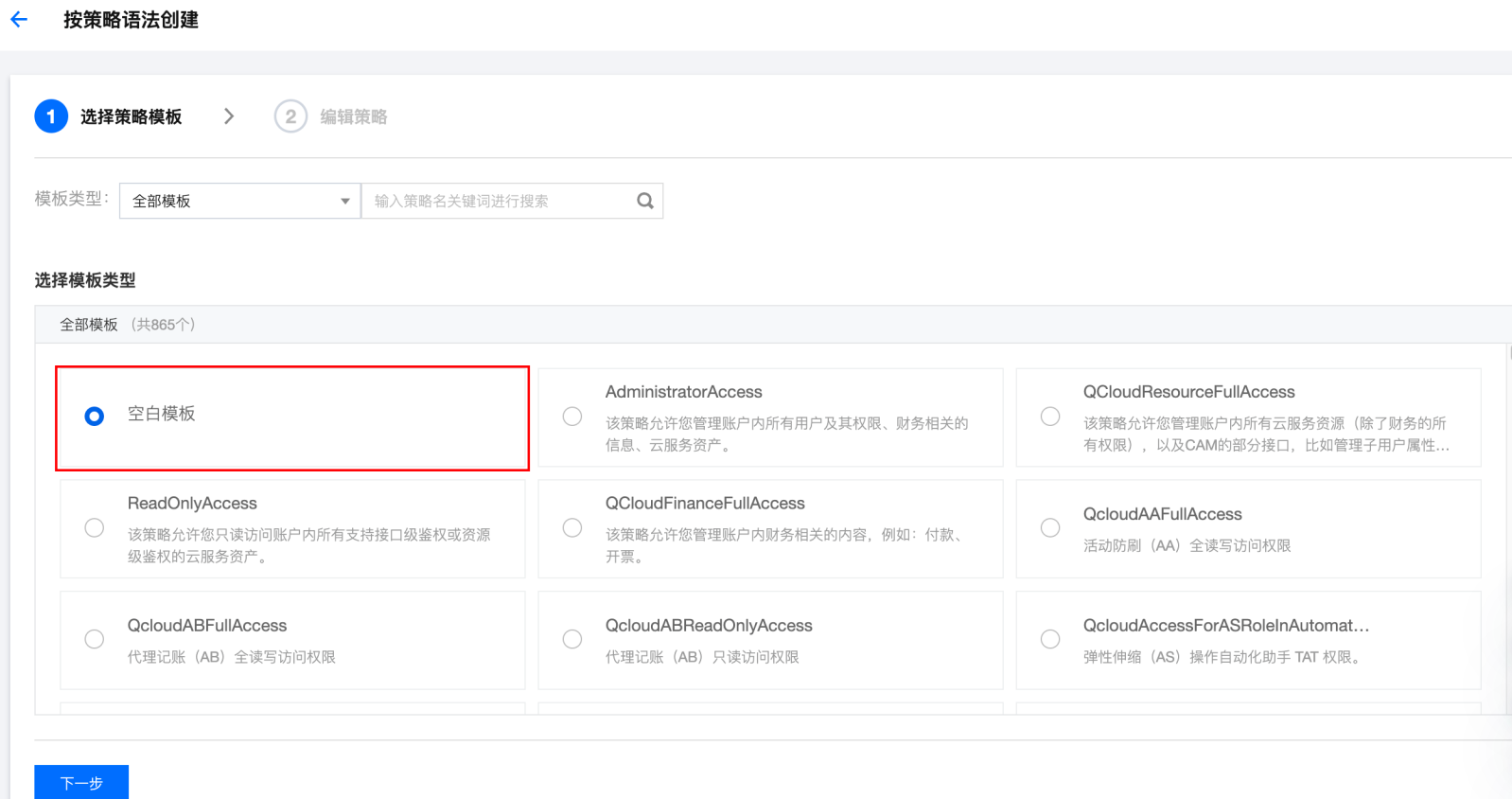
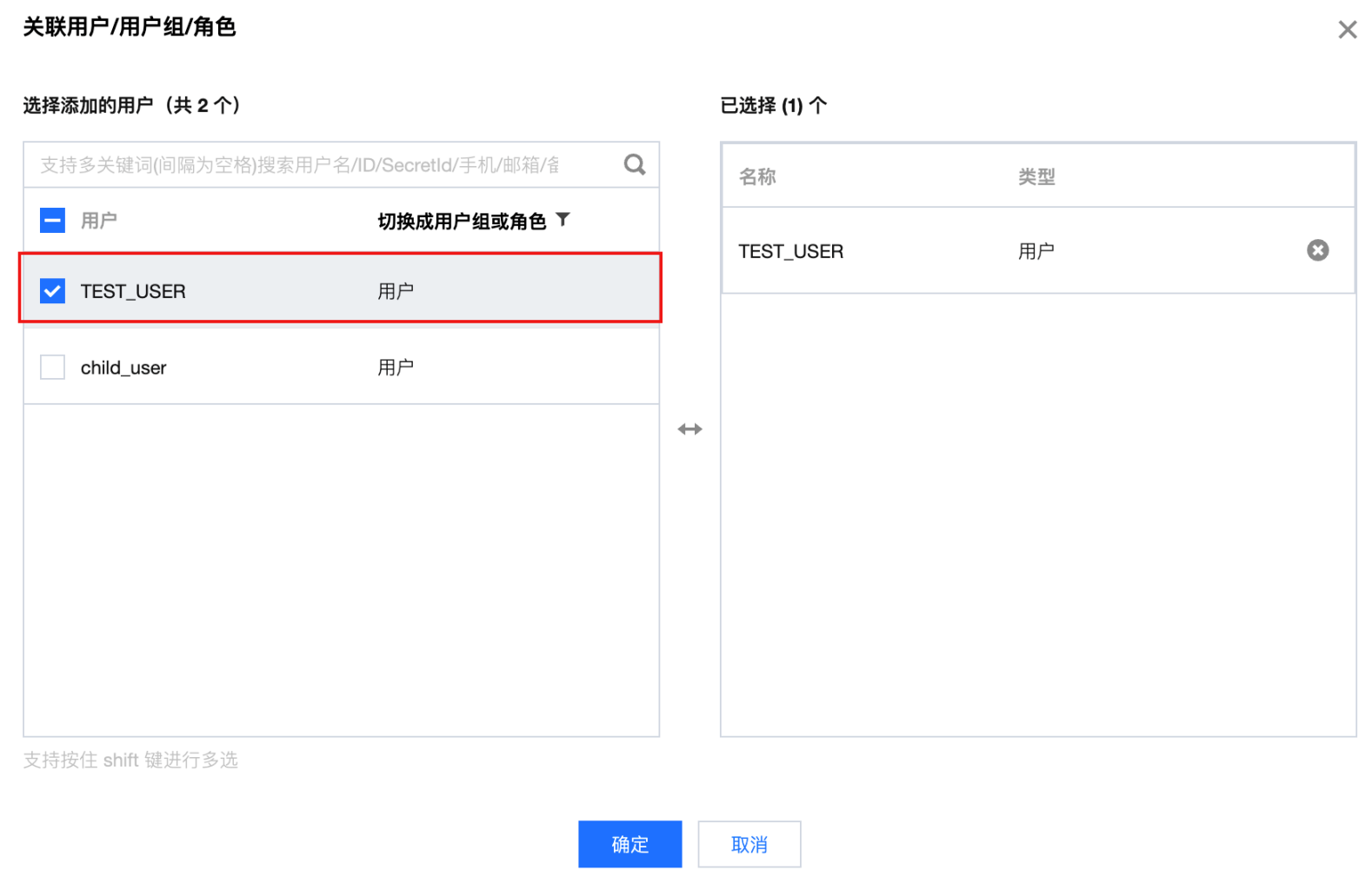
步骤1:通过 AKSK 授权方式配置认证信息
{"statement": [{"action": ["ssm:GetSecretValue"],"effect": "allow","resource": ["qcs::ssm:$region:uin/$uin:secret/creatorUin/$creatorUin/$secretName"]}],"version": "2.0"}
步骤2:组件使用说明
SecretName: hello-testSecretData: {"name":"jack","password":"123"}VersionId: v1
echo -n 'KEYID' > ./accessKeyIdecho -n 'SECRETKEY' > ./accessKeySecretkubectl create secret generic tencent-credentials --from-file=./accessKeyId --from-file=./accessKeySecret
apiVersion: external-secrets.io/v1beta1 kind: SecretStore metadata:
name: my-secretstore spec: provider: tencent: regionID: ap-guangzhou
auth: secretRef: accessKeyIDSecretRef: name: tencent-credentials key:
accessKeyId accessKeySecretSecretRef: name: tencent-credentials key: accessKeySecret
apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata: name:
my-externalsecret spec: refreshInterval: 1m secretStoreRef: kind: SecretSt
ore name: my-secretstore target: name: my-secret-key-to-be-created creation
Policy: Owner data: - secretKey: secret-key-to-be-managed remoteRef: key:
hello-test version: v1 # option property: password
kubectl apply -f my-secretstore.yaml kubectl apply -f my-externalsecret.yaml
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container
image: busybox command: - /bin/sh - -c - 'echo "Secret value: ${SECRET_KEY_TO_
BE_MANAGED}"' env: - name: SECRET_KEY_TO_BE_MANAGED valueFrom: secretKeyRef:
name: my-secret-key-to-be-created key: secret-key-to-be-managed restartPolicy: Never
kubectl apply -f my-pod.yaml
kubectl logs my-pod
# ExternalSecret中获取的凭据信息如下所示。 Secret value: 123
方式二:通过 AKSK 与角色扮演授权
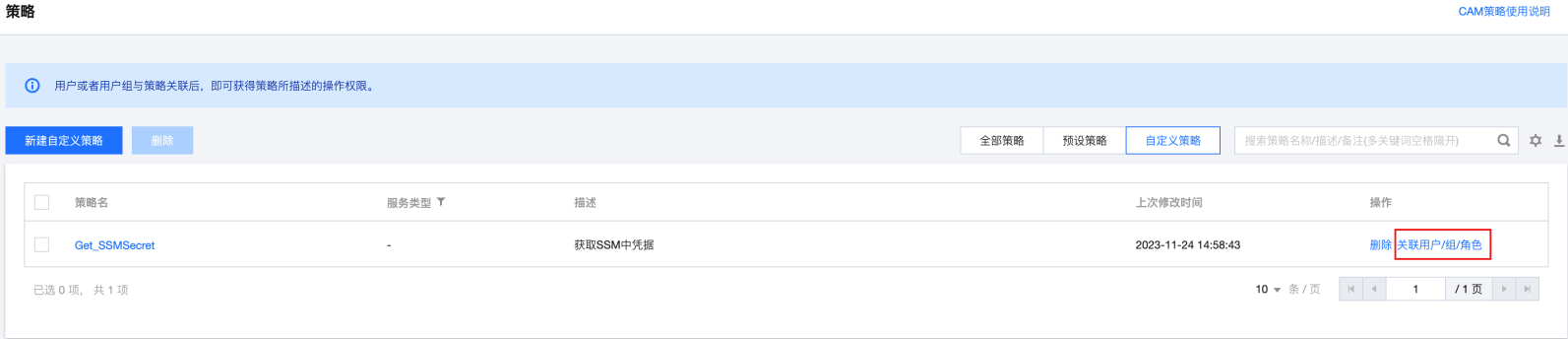
步骤1:创建获取 SSM 凭据的策略
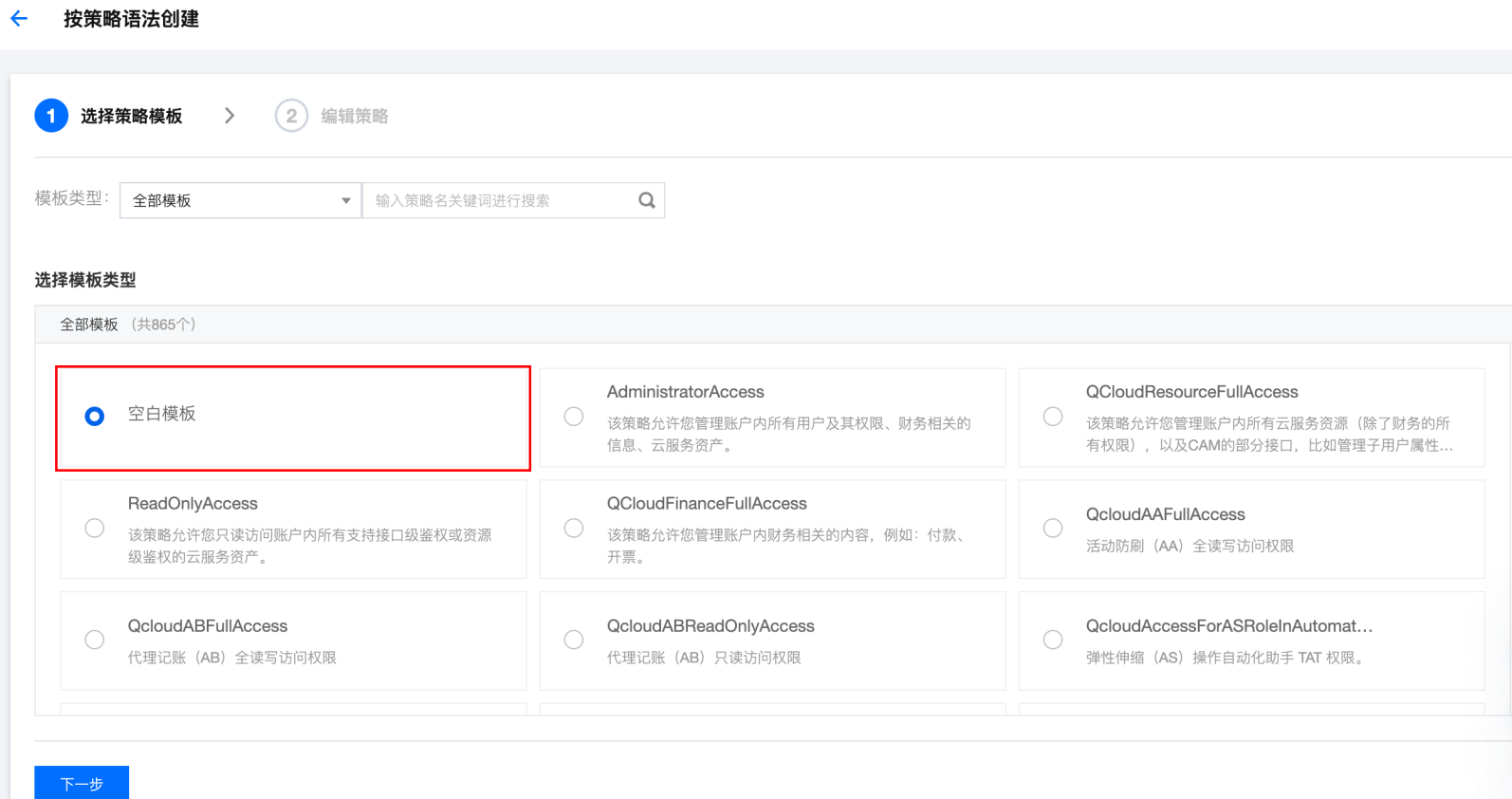
{"statement": [{"action": ["ssm:GetSecretValue"],"effect": "allow","resource": ["qcs::ssm:$region:uin/$uin:secret/creatorUin/$creatorUin/$secretName"]}],"version": "2.0"}
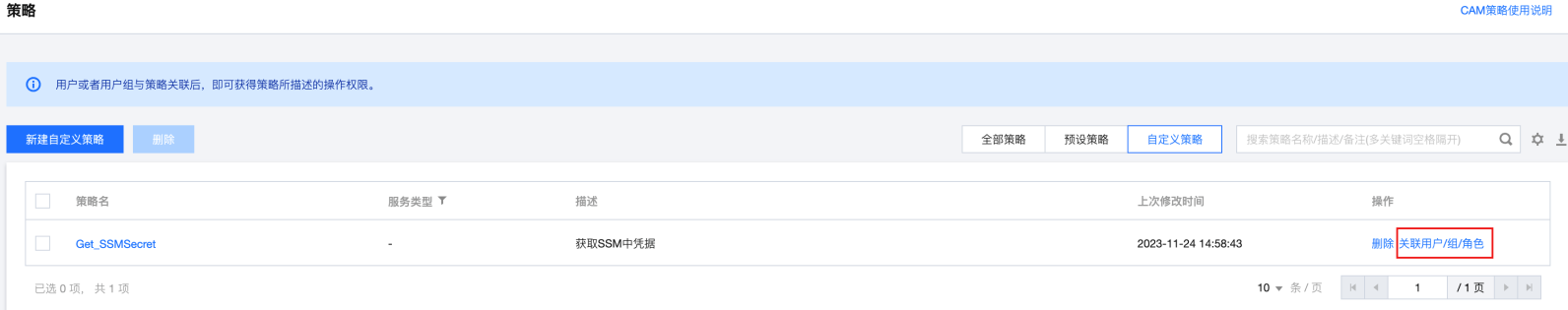
步骤2:为子账号赋予扮演角色策略
步骤3:为角色赋予访问 SSM 凭据的策略
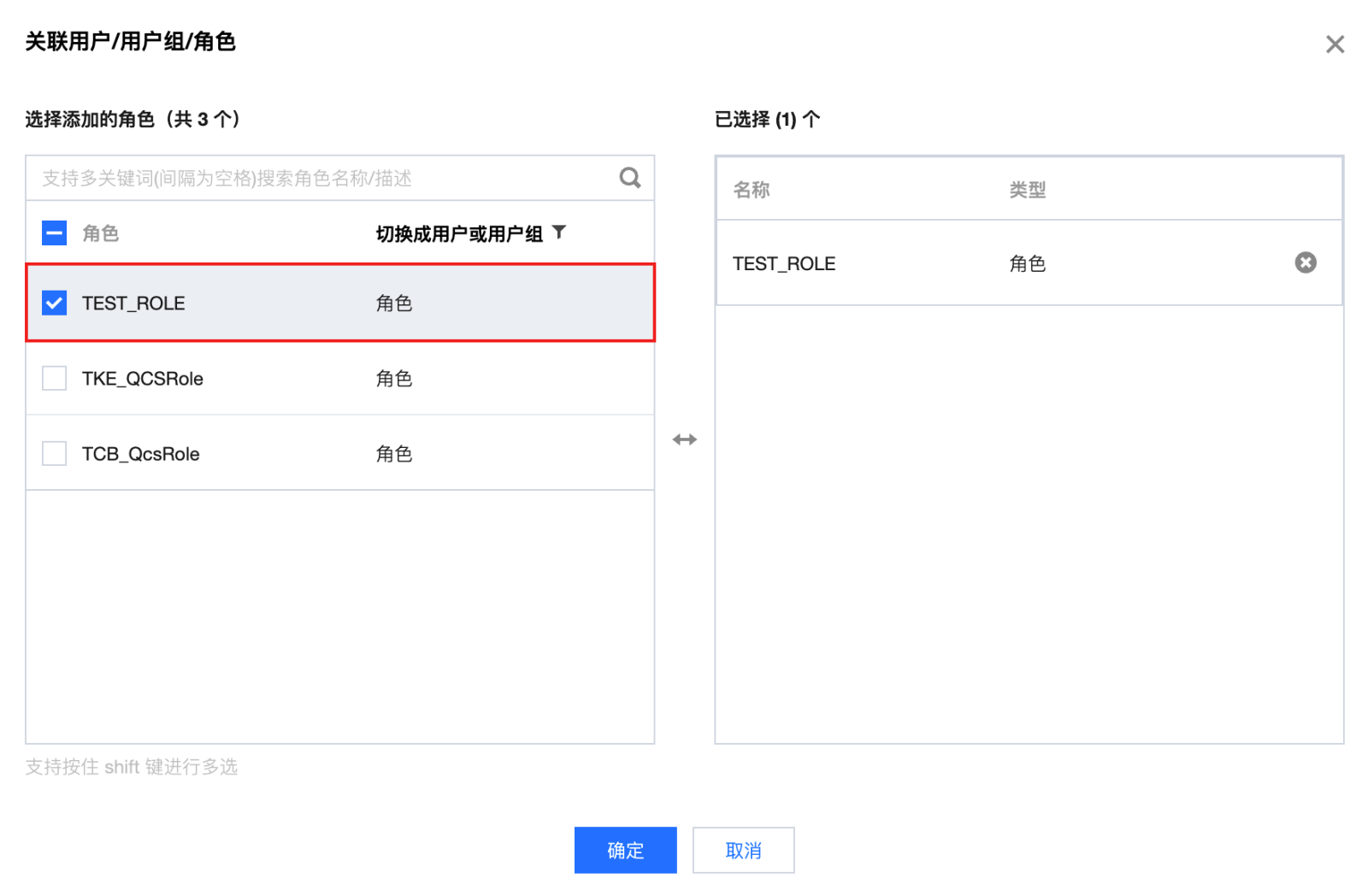
步骤4:组件使用说明
SecretName: hello-testSecretData: {"name":"jack","password":"123"}VersionId: v1
echo -n 'KEYID' > ./accessKeyIdecho -n 'SECRETKEY' > ./accessKeySecretkubectl create secret generic tencent-credentials --from-file=./accessKeyId --from-file=./accessKeySecret
apiVersion: external-secrets.io/v1beta1 kind: SecretStore metadata: name:
secretstore-assumerole spec: provider: tencent: regionID: ap-guangzhou role:
"qcs::cam::uin/12345:roleName/test-assume-role" auth: secretRef: accessKeyIDSec
retRef: name: tencent-credentials key: accessKeyId accessKeySecretSecretRef:
name: tencent-credentials key: accessKeySecret
apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata:
name: external-secret-assumerole spec: refreshInterval: 1m secretStoreRef:
kind: SecretStore name: secretstore-assumerole target: name: my-secret-key
-to-be-created creationPolicy: Owner data: - secretKey: secret-key-to-be-
managed remoteRef: key: hello-test version: v1 property: password
kubectl apply -f my-secretstore.yaml kubectl apply -f my-externalsecret.yaml
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name:
my-container image: busybox command: - /bin/sh - -c - 'echo "Secret value:
${SECRET_KEY_TO_BE_MANAGED}"' env: - name: SECRET_KEY_TO_BE_MANAGED valueFrom:
secretKeyRef: name: my-secret-key-to-be-created key: secret-key-to-be-managed restartPolicy: Never
kubectl apply -f my-pod.yaml
kubectl logs my-pod
# ExternalSecret中获取的凭据信息如下所示。 Secret value: 123
方式三:通过 TKE OIDC 授权
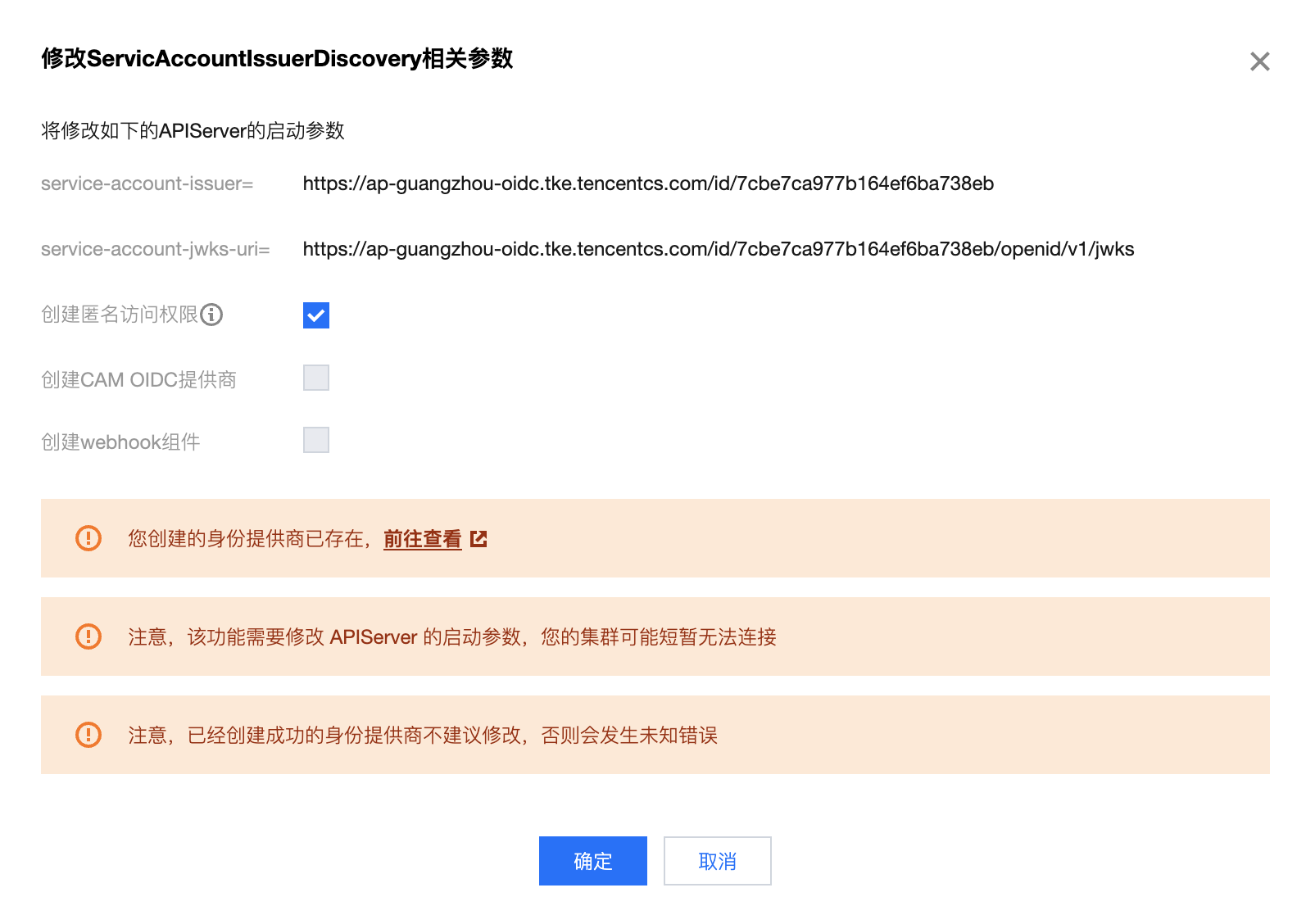
步骤1:开启 OIDC 资源访问控制能力

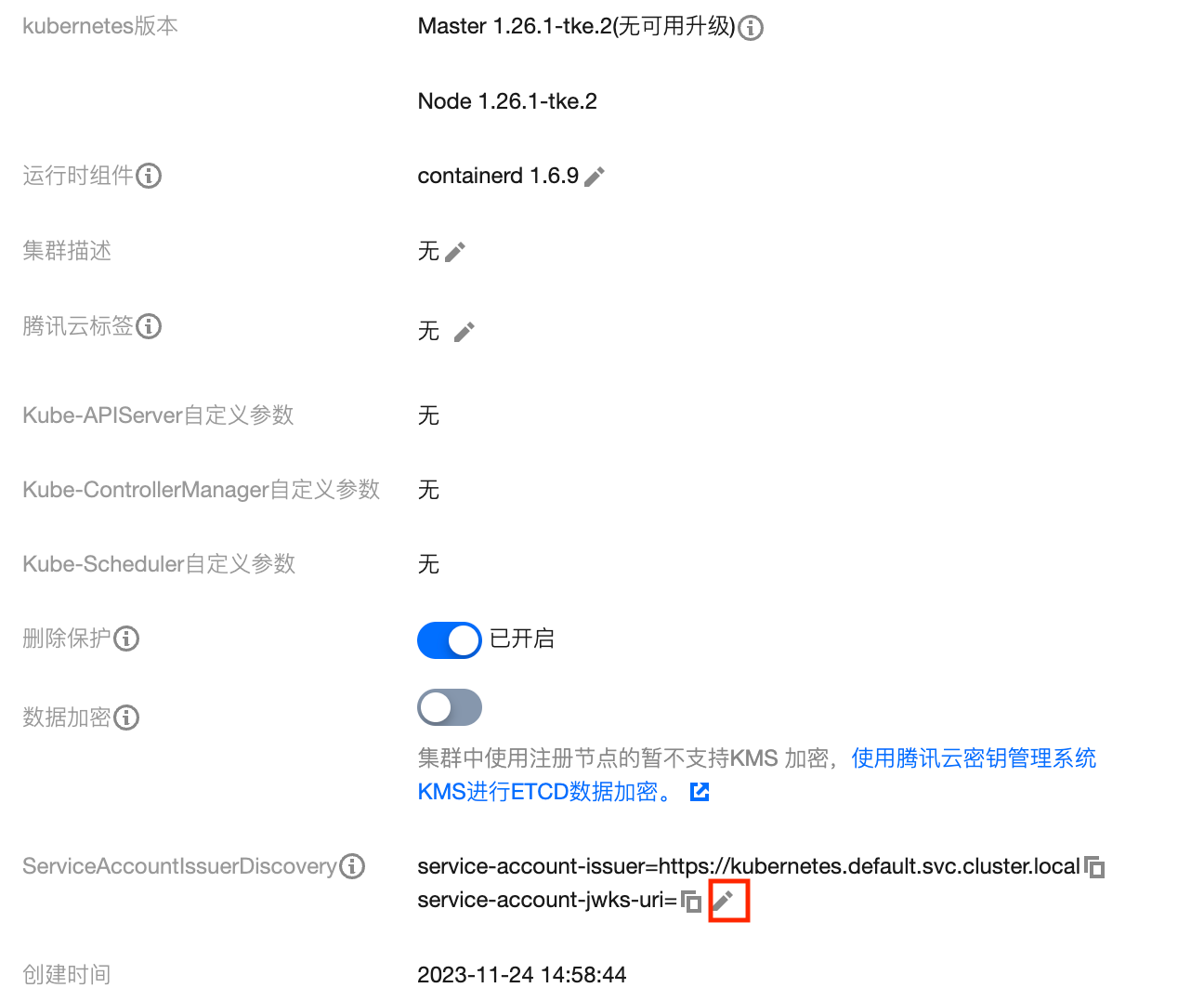
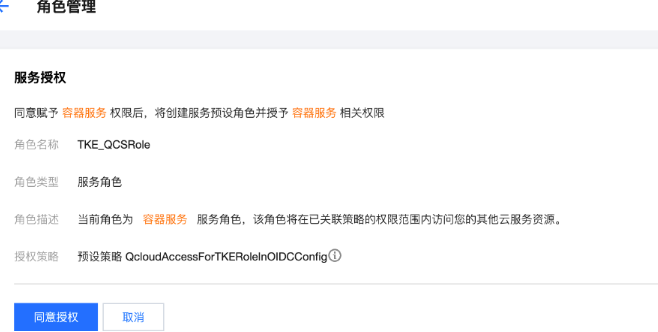
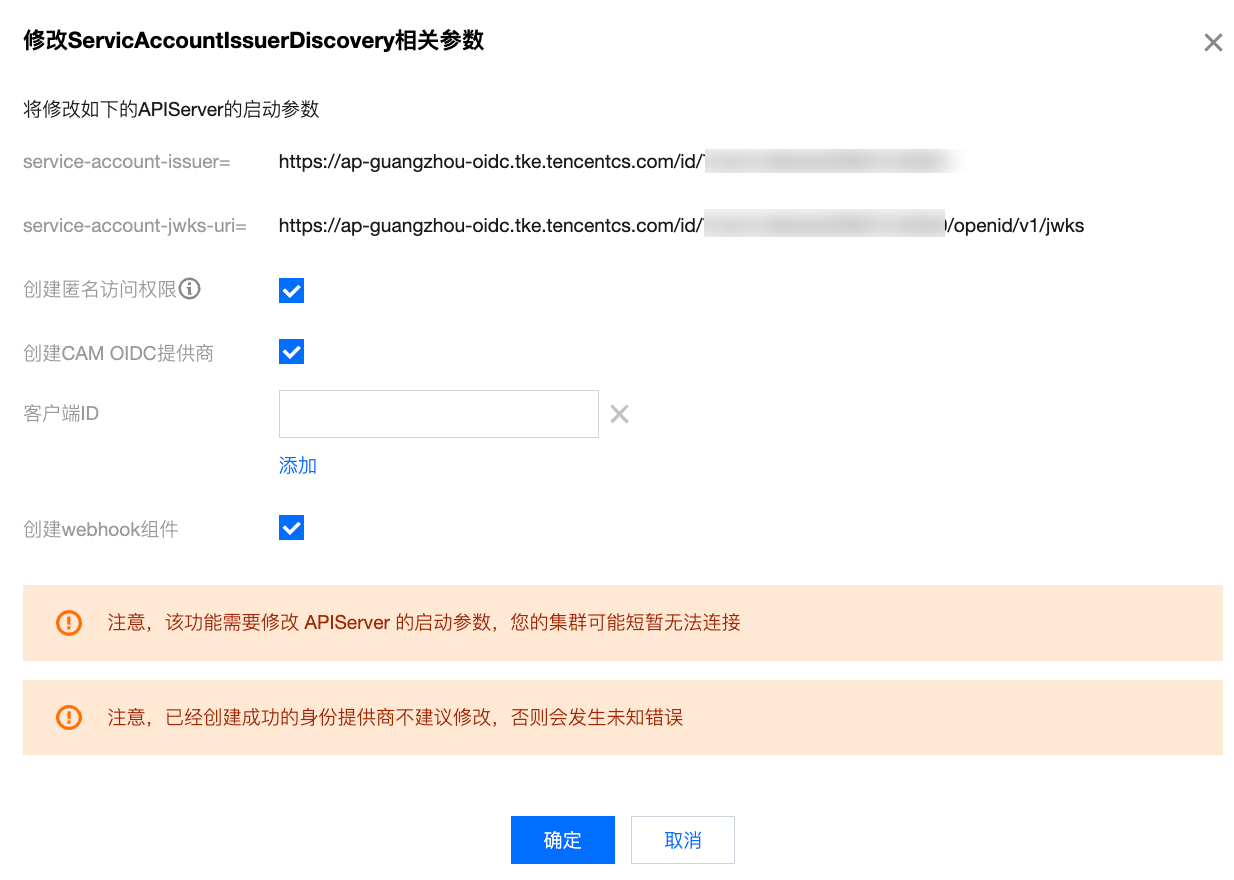 6. 返回集群详情页,当 ServiceAccountIssuerDiscovery 可再次编辑时,表明本次开启 OIDC 资源访问控制结束。
6. 返回集群详情页,当 ServiceAccountIssuerDiscovery 可再次编辑时,表明本次开启 OIDC 资源访问控制结束。
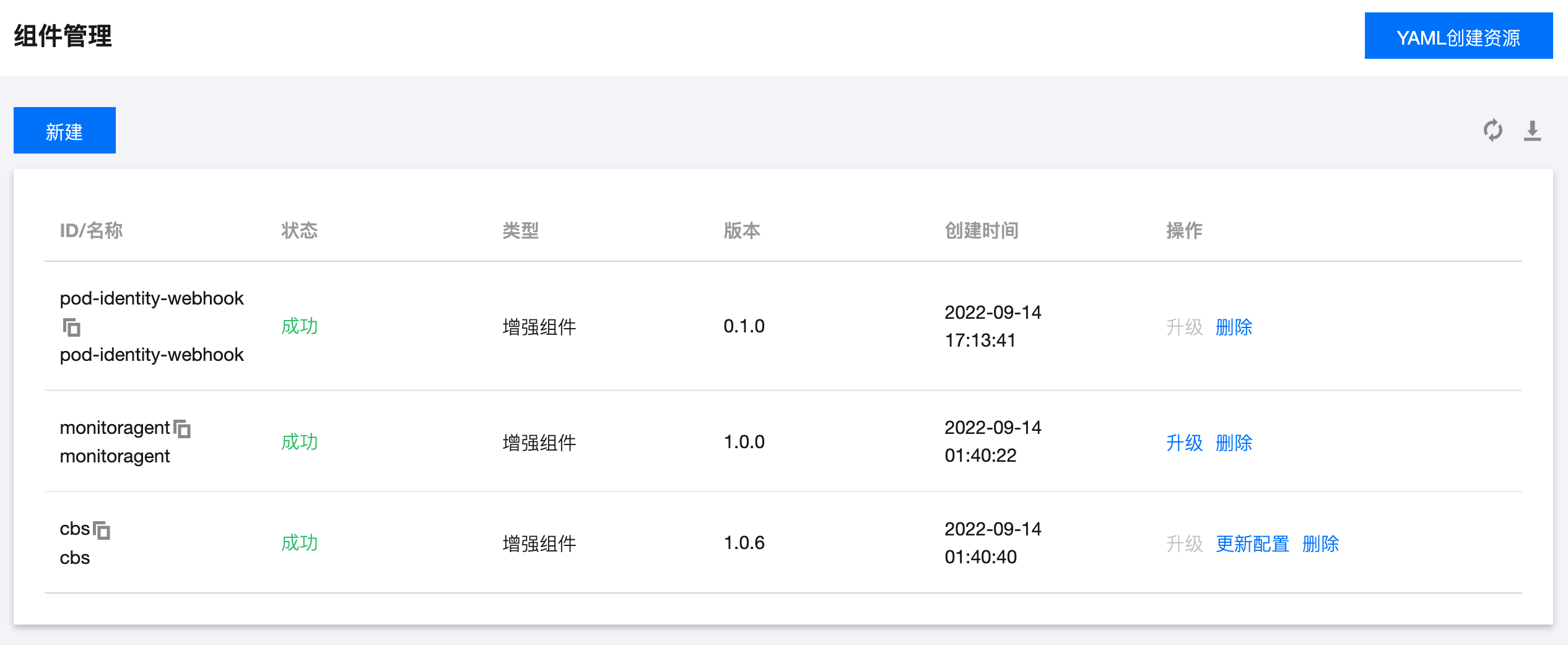
步骤2:创建获取 SSM 凭据的策略
{"statement": [{"action": ["ssm:GetSecretValue"],"effect": "allow","resource": ["qcs::ssm:$region:uin/$uin:secret/creatorUin/$creatorUin/$secretName"]}],"version": "2.0"}
步骤3:新建 OIDC 角色
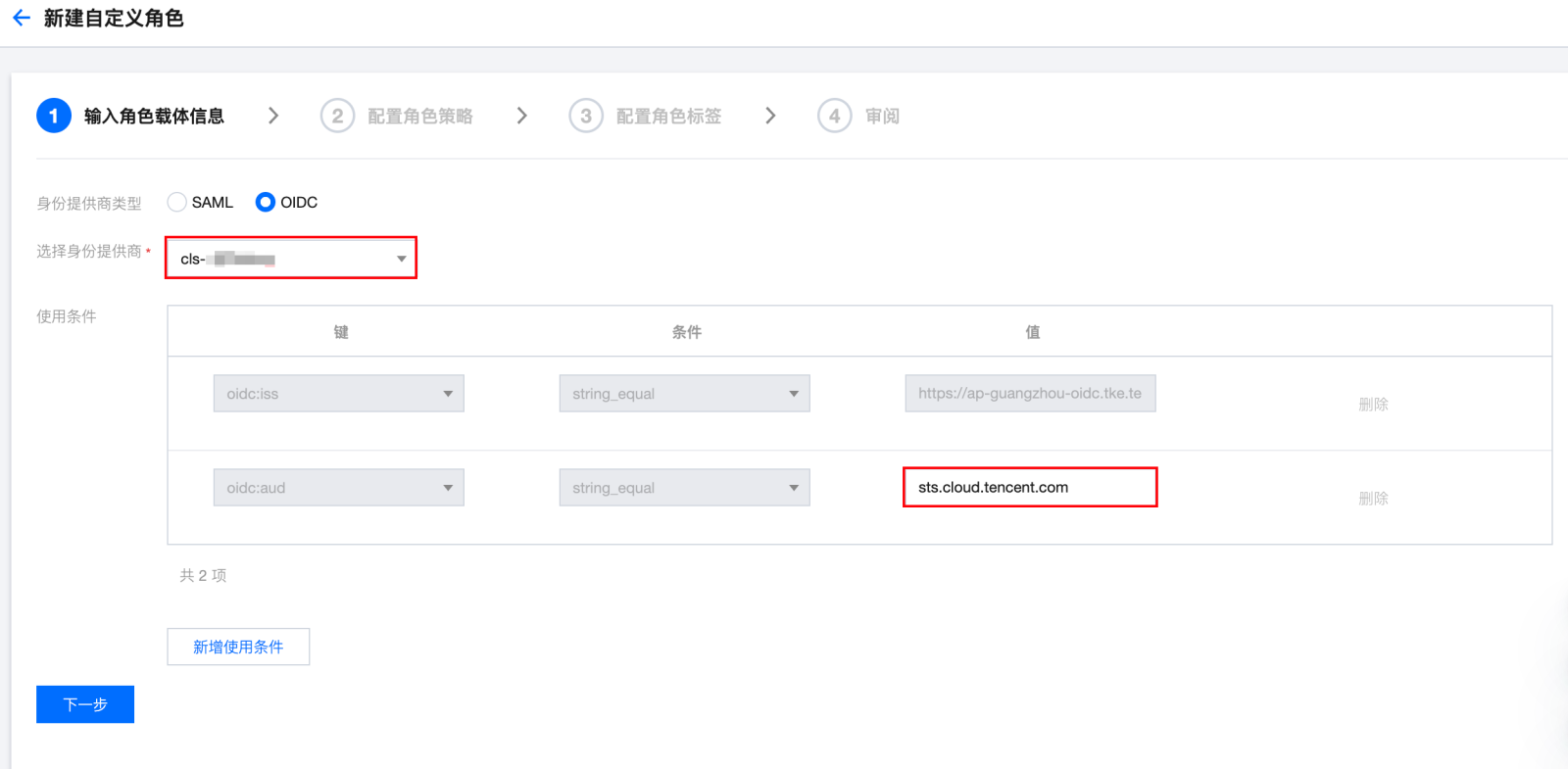
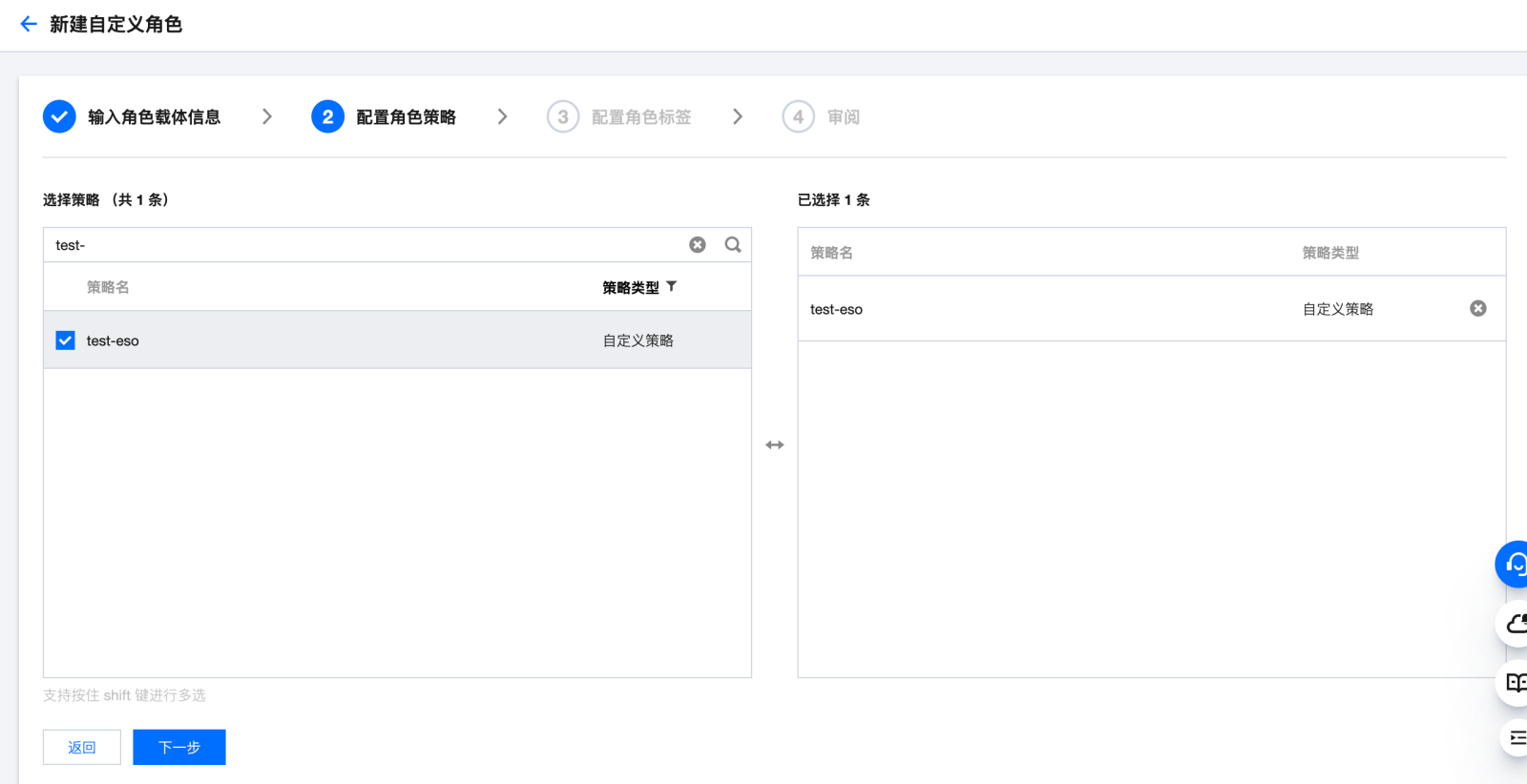
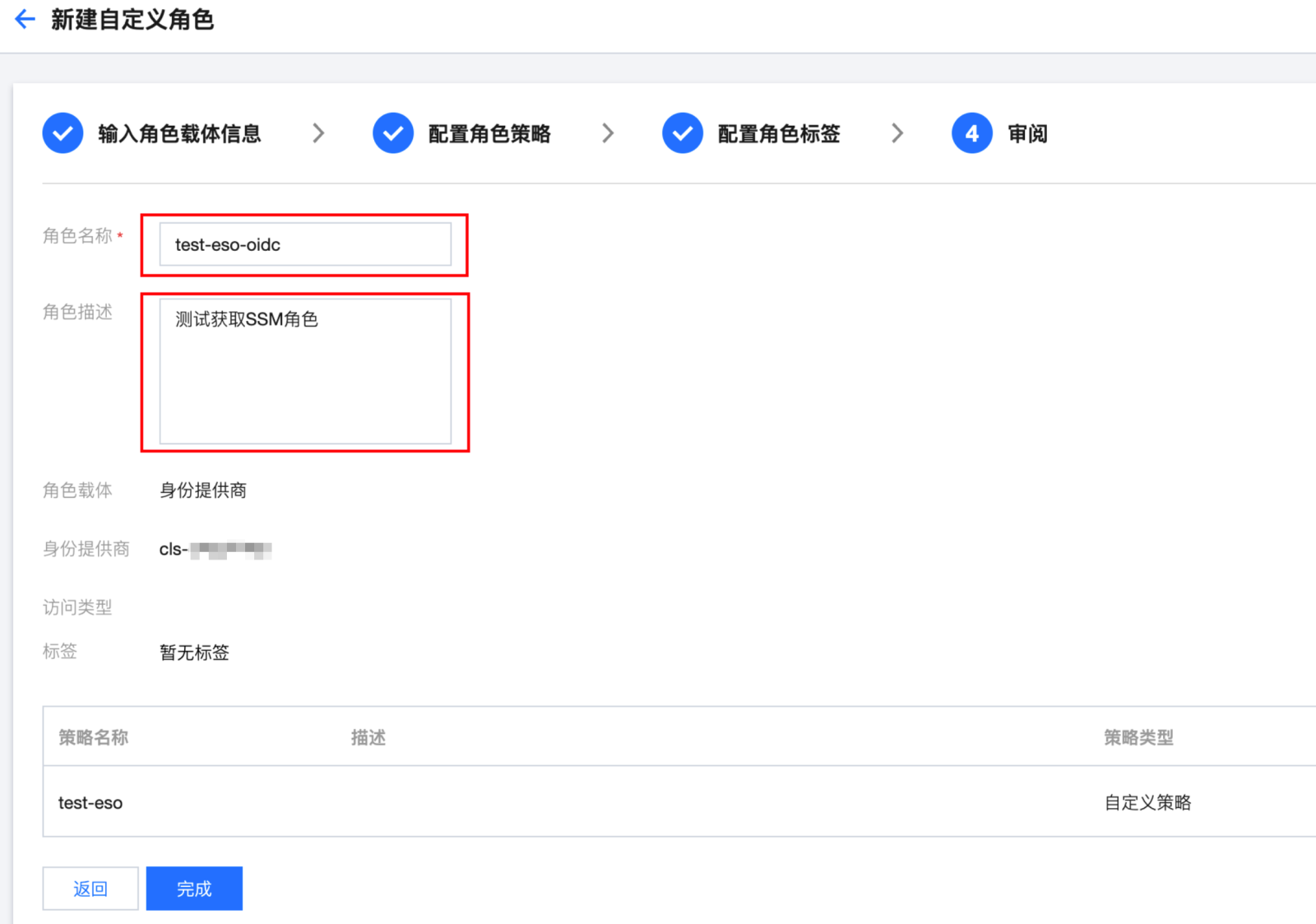
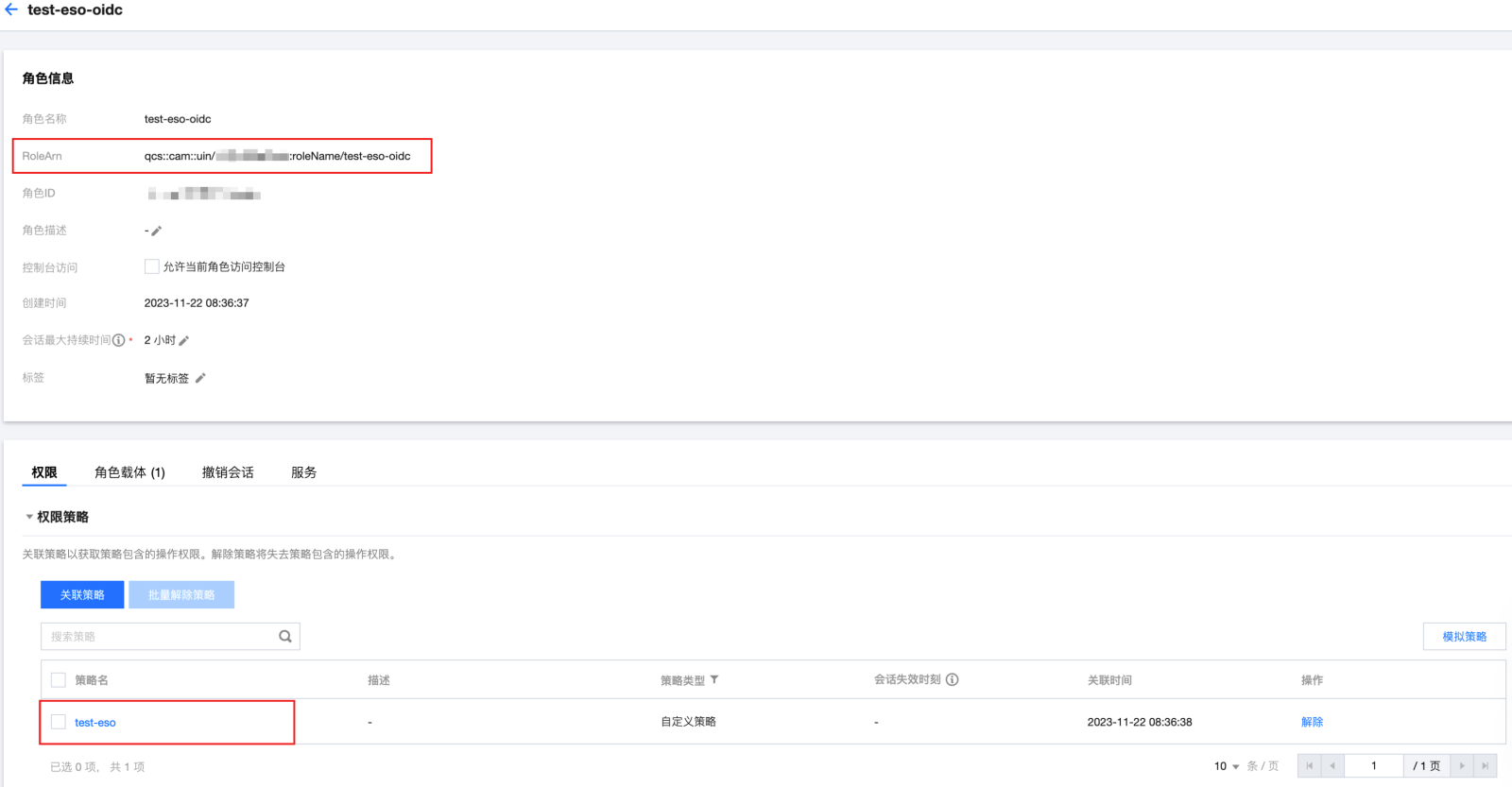
步骤4:组件使用说明
apiVersion: v1 kind: ServiceAccount metadata: name: my-serviceaccount annotations:
tke.cloud.tencent.com/role-arn: $my_pod_role_arn tke.cloud.tencent.com/audience:
$my_pod_audience tke.cloud.tencent.com/providerID: $my_provider_id
apiVersion: external-secrets.io/v1beta1 kind: SecretStore metadata: name:
secretstore-tkeoidc spec: provider: tencent: regionID: ap-guangzhou auth:
serviceAccountRef: name: my-serviceaccount
apiVersion: external-secrets.io/v1beta1 kind: ExternalSecret metadata:
name: external-secret-tkeoidc spec: refreshInterval: 1h secretStoreRef:
kind: SecretStore name: secretstore-tkeoidc target: name: my-secret-key-
to-be-created creationPolicy: Owner data: - secretKey: secret-key-to-be-
managed remoteRef: key: hello-test version: v1 # option property: password
kubectl apply -f my-serviceaccount.yaml kubectl apply -f my-secretstore.yaml kubectl apply -f my-externalsecret.yaml
kubectl get secret my-secret-key-to-be-created -o yaml






