本文档介绍如何通过YAML创建和管理CCE Ingress。
创建Ingress Controller资源
使用以下yaml内容创建Ingress Controller:
kubectl create -f ingress-controller.yaml
ingress-controller.yaml 如下所示:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
namespace: kube-system
name: cce-ingress-clusterrole
rules:
- apiGroups: [""]
resources:
- nodes
- services
verbs: ["get", "list", "watch"]
- apiGroups: ["extensions"]
resources:
- ingresses
verbs: ["get", "list", "watch", "update", "patch"]
- apiGroups: [""]
resources:
- events
verbs: ["create", "update", "patch"]
- apiGroups:
- "extensions"
resources:
- ingresses/status
verbs:
- update
---
apiVersion: v1
kind: ServiceAccount
metadata:
namespace: kube-system
name: cce-ingress-serviceaccount
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
namespace: kube-system
name: cce-ingress-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cce-ingress-clusterrole
subjects:
- kind: ServiceAccount
namespace: kube-system
name: cce-ingress-serviceaccount
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: cce-ingress-controller
namespace: kube-system
spec:
replicas: 1
selector:
matchLabels:
app: cce-ingress-controller
template:
metadata:
labels:
app: cce-ingress-controller
spec:
hostNetwork: true
serviceAccountName: cce-ingress-serviceaccount
dnsPolicy: ClusterFirst
restartPolicy: Always
terminationGracePeriodSeconds: 30
containers:
- name: ingress-controller
image: hub.baidubce.com/cce/cce-ingress-controller:latest
imagePullPolicy: Always
volumeMounts:
- name: etc-volume
mountPath: /etc/kubernetes/
readOnly: true
resources:
limits:
cpu: 0.5
memory: 500Mi
volumes:
- name: etc-volume
hostPath:
path: /etc/kubernetes/
创建示例 Deployment 和 Service
apiVersion: apps/v1
kind: Deployment
metadata:
name: ingress-nginx-deployment
labels:
app: ingress-nginx
spec:
replicas: 2
selector:
matchLabels:
app: ingress-nginx
template:
metadata:
labels:
app: ingress-nginx
spec:
containers:
- name: nginx
image: hub.baidubce.com/cce/nginx-ingress
ports:
- containerPort: 80
---
kind: Service
apiVersion: v1
metadata:
name: hello-service
spec:
selector:
app: ingress-nginx
type: NodePort
ports:
- protocol: TCP
port: 8000
targetPort: 80
---
kind: Service
apiVersion: v1
metadata:
name: world-service
spec:
selector:
app: ingress-nginx
type: NodePort
ports:
- protocol: TCP
port: 9000
targetPort: 80
创建Ingress对象
使用以下yaml内容创建名为 helloworld 的 Ingress 对象,并配置Ingress转发规则:
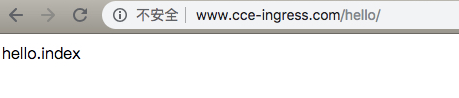
- www.cce-ingress.com/hello/ -> hello-service:8000/hello/
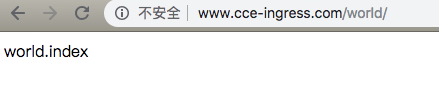
- www.cce-ingress.com/world/ -> world-service:9000/world/
可通过Ingress annotations中的参数对Ingress进行配置,例如指定BLB或EIP。
Service 对应后端服务必须支持转发策略的 URI,如果要支持所有情况,建议设置为 /*,这里对URI的路径要求很严格注意"/"。
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
cce.ingress.blb-backup-content: ""
kubernetes.io/cce.ingress.blb-cert-id: ""
kubernetes.io/cce.ingress.blb-id: ""
kubernetes.io/cce.ingress.eip: ""
kubernetes.io/cce.ingress.http-redirect: "false"
kubernetes.io/cce.ingress.https: "false"
kubernetes.io/cce.ingress.internal: "false"
kubernetes.io/cce.ingress.timeout-in-seconds: "30"
kubernetes.io/cce.ingress.vpc-subnet-id: ""
kubernetes.io/ingress.class: cce
name: helloworld
namespace: default
spec:
rules:
- host: www.cce-ingress.com
http:
paths:
- backend:
serviceName: hello-service
servicePort: 8000
path: /hello/
- backend:
serviceName: world-service
servicePort: 9000
path: /world/
访问测试
修改本地 /etc/hosts,将 www.cce-ingress.com 指向 EIP(例如: 106.12.52.80),可在控制台或者集群内查看ingress信息:
# kubectl get ingress
NAME HOSTS ADDRESS PORTS AGE
helloworld www.cce-ingress.com 10.0.3.251,106.12.52.80 80 6m34s
访问测试:
Ingress Annotation 说明
| 参数名 | 类型 | 说明 | 示例 |
|---|---|---|---|
| kubernetes.io/ingress.class | string | 指定为 cce-ingress-controller 托管 | "cce" |
| kubernetes.io/cce.ingress.keep-iaas-resource | string | 释放时是否保留 BLB/EIP | "true" 或 "false", 默认 false |
| kubernetes.io/cce.ingress.blb-name | string | 指定 Ingress 对应 BLB Name | 为避免 CCE 默认 Name 超长,支持指定 BLB Name |
| kubernetes.io/cce.ingress.enable-ipv6 | string | 在IPv6 集群中使用,会为 Ingress 分配 IPv6 地址 | "true" 或 "false",默认为 "false" |
| kubernetes.io/cce.ingress.blb-id | string | Ingress 绑定 BLB,修改或删除可能会导致 BLB 泄漏 | "lb-asdfDsXS" |
| kubernetes.io/cce.ingress.internal | string | 是否只内网访问,默认 "false" | "true" 或 "false" |
| kubernetes.io/cce.ingress.eip | string | Ingress 绑定 EIP,修改或删除可能会导致 EIP 泄漏 | "100.0.0.1" |
| kubernetes.io/cce.ingress.eip-bandwidth-in-mbps | string | EIP 带宽,按流量计费 1~1000 mbps | "500" |
| kubernetes.io/cce.ingress.timeout-in-seconds | string | 访问超时时间 1~3600 | "1500" |
| kubernetes.io/cce.ingress.https | string | 是否支持 HTTPS | "true" 或 "false" |
| kubernetes.io/cce.ingress.http-redirect | string | HTTP 是否支持 HTTPS 重定向,开启 HTTPS 才生效 | "true" 或 "false" |
| kubernetes.io/cce.ingress.blb-cert-id | string | HTTPS 证书 ID | "xs-asdfDESz" |
| kubernetes.io/cce.ingress.max-backend-count | string | BLB 挂载默认 RS 数,默认不做限制 | "50" |
| kubernetes.io/cce.ingress.vpc-subnet-id | string | 指定 BLB VPC 子网,默认不使用 | "sb-adfEsDzs" |
CCE Ingress 为满足单个域名同时支持 HTTP 及 HTTPS 转发,新增如下两条 Annotation:
kubernetes.io/cce.ingress.http-rules:
[
{
"host":"baidu-cce-ingress.com",
"http":{
"paths":[
{
"path":"/apple/",
"backend":{
"serviceName":"service-example",
"servicePort":80
}
},
{
"path":"/banana/",
"backend":{
"serviceName":"service-example",
"servicePort":80
}
}
]
}
}
]
kubernetes.io/cce.ingress.https-rules
[
{
"host":"baidu-cce-ingress.com",
"http":{
"paths":[
{
"path":"/orange/",
"backend":{
"serviceName":"service-example",
"servicePort":80
}
}
]
}
}
]
规则逻辑如下:
for rule in rules:
if rule in annotation_https_rules:
setHTTPS(rule)
if rule in annotation_http_rule:
setHTTP(rule)
if rule not in annotation_https_rules && rule not in annotation_http_rule:
setHTTP(rule)






